MGT300 - CHAPTER 5
CHAPTER 5 : ORGANIZATIONAL STRUCTURES THAT SUPPORT STRATEGIC INITIATIVES
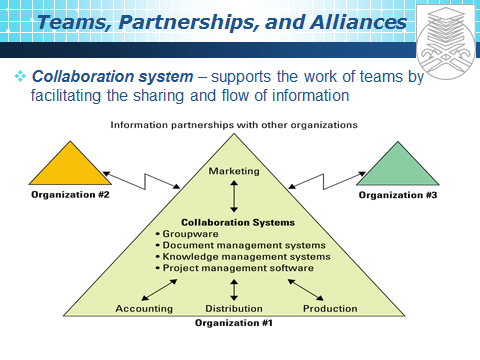
Organizational Structures
- Organizational employees must work closely together to develop strategic initiatives that create competitive advantages
- Ethics and security are two fundamental building blocks that organizations must base their businesses upon
IT Roles and responsibilities
- Information technology is a relatively new functional area, having only been around formally for around 40 years
- Recent IT-related strategic positions :
- Chief Technology Officer ( CTO)
- Chief Security Officer (CSO )
- Chief Privacy Officer (CPO )
- Chief Knowledge Office ( CKO )
1. Chief Information Officer ( CIO )
- Chief Information Officer ( CIO ) - oversees all uses of IT and ensures that strategic alignment of IT with business goal and objectives
- Broad CIO functions include :
- Leader - ensuring the strategic vision of IT is in line with the strategic vision of the organization
- Communicator - building and maintaining strong executive relationship
2. Chief Technology Officer ( CTO )
Responsible for ensuring the throughput, speed, accuracy, availability, and reliability of IT
3. Chief Security Officer ( CSO )
Responsible for ensuring the security of IT system
4. Chief Privacy Officer ( CPO )
Responsible for ensuring the ethical and legal use of information
5. Chief Knowledge Officer ( CKO )
Responsible for collecting. maintaining and distributing the organization's knowledge
The Gap Between Business Personnel and IT Personnel
- Business personnel possess expertise in functional areas such as marketing, accounting and sales
- IT personnel have the technical expertise
- This typically causes a communication gap between the business personnel and IT personnel
Improving Communications
- Business personnel must seek to increase their understanding of IT
- IT personnel must seek to increase their understanding of the business
- It is the responsibility of the CIO to ensure effective communication between business personnel and IT personnel
Organizational Fundamentals - Ethics and Security
- Ethics and security are two fundamentals building blocks that organization must base their businesses on to be successful
- In recent years, such events such as the Entron and Martha Steward, along with 9/11 have shed new light on the meaning of ethics and security
- Ethics - the principles and standards that guide our behavior toward other people
- Privacy - the right to be left alone when you want to be, to have control over your own personnel possessions, and not to be observed without your consent
Ethics
- Issues affected by technology advance :
- Intellectual property
- Copyright
- Fair use doctrine
- Pirated software
- Counterfeit software
1. Intellectual property
Intangible creative work that is embodied in physical form
2. Copyright
The legal protection afforded an expression of an idea, such as a song, video games and some types of proprietary documents
3. Fair use doctrine
In certain situations, it is legal to use copyrighted material
4. Pirated software
The unauthorized use, duplication, distribution, or sale of copyrighted software
5. Counterfelt software
Software that is manufactured to look like the real thing and sold as such
- One of the main ingredients in trust is privacy
- Primary reason privacy issues lost trust of e-business
- Loss of personal privacy is a top concern for Americans in 21st century
- Among internet users, 37 percent would be a 'LOT' more inclined to purchase a product on a website that had privacy policy
Property
- Organizational information is intellectual capital- it must be protect
- Information security - the protection of information from accidental or intentional misuse by person inside or outside an organization
- E- business automatically create tremendous information security risks for organizations.





Comments
Post a Comment